No matter how advanced your defenses are, cyber incidents are inevitable—what matters most is how you respond. An ineffective response can escalate a breach into a crisis. For CISOs, CTOs, and compliance leaders, having a robust, well-practiced Cyber Incident Response Plan (CIRP) is essential for containing damage, restoring operations, and meeting regulatory obligations.
In this blog, we’ll break down the six critical steps of an incident response framework and explore how to build a plan that actually works under pressure.
-
A Cyber Incident Response Plan (CIRP) outlines how to detect, respond to, and recover from security incidents.
-
The 6 phases include: preparation, identification, containment, eradication, recovery, and lessons learned.
-
Plans should be regularly tested, updated, and integrated into your enterprise risk strategy.
-
A well-executed CIRP can reduce downtime, limit data exposure, and ensure regulatory compliance.
What is a Cyber Incident Response Plan?
A Cyber Incident Response Plan is a documented process that guides your organization in identifying, managing, and recovering from cyber threats such as:
-
Ransomware attacks
-
Insider threats
-
Data breaches
-
DDoS attacks
-
Supply chain vulnerabilities
This plan ensures roles, tools, and workflows are clearly defined ahead of a breach. The goal? Minimize the impact, protect sensitive data, and restore normal operations quickly.
What is the purpose of an incident response plan in cybersecurity?
The purpose is to provide a structured approach to identifying and managing cybersecurity incidents to limit damage and recovery time.
The 6 Essential Steps of a Cyber Incident Response Framework
1. Preparation: Laying the Groundwork
Preparation is the foundation of incident response. It includes:
-
Developing policies, procedures, and communication workflows
-
Building an internal response team
-
Running tabletop exercises and simulations
-
Ensuring tools like SIEM, SOAR, and endpoint detection systems are in place
📌 Pro tip: According to IBM’s Cost of a Data Breach Report 2023, organizations with an IR team and tested plan saved $2.66 million on average compared to those without.
2. Identification: Spotting the Threat
In this stage, the focus is on detecting abnormal activity through:
-
Network monitoring tools
-
Endpoint alerts
-
Threat intelligence feeds
-
User reports
Key outcomes:
-
Classify the incident (malware, phishing, insider threat, etc.)
-
Determine its severity and scope
-
Document initial indicators of compromise (IOCs)
How do you identify a cyber incident?
By analyzing system logs, alerts, and reports for anomalies or known indicators of compromise.
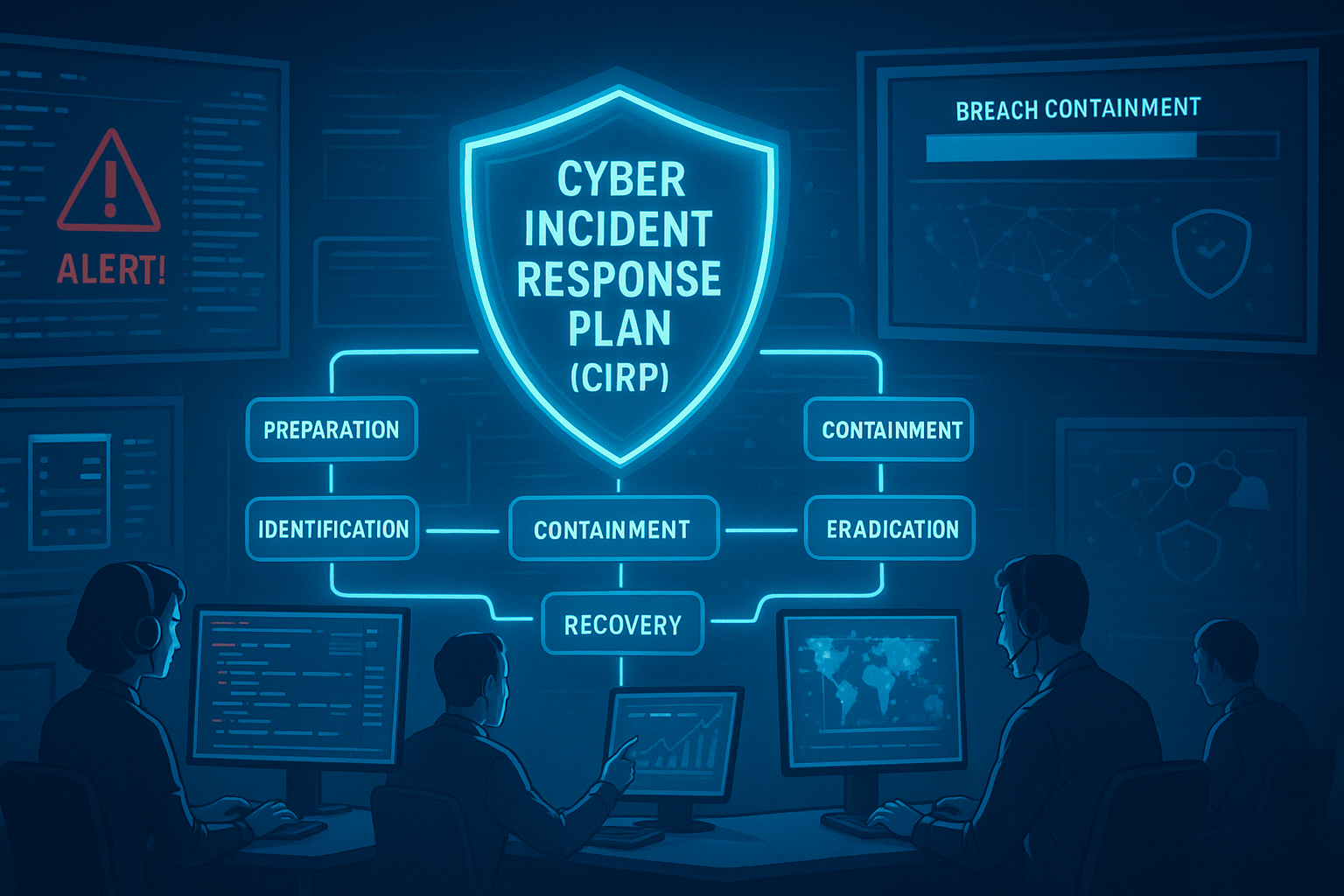
3. Containment: Stopping the Spread
Once an incident is identified, containment prevents it from causing further harm. This can include:
-
Isolating affected systems
-
Changing passwords
-
Blocking malicious IPs or domains
-
Temporarily disabling vulnerable services
Short-term vs. long-term containment strategies may differ based on threat complexity.
4. Eradication: Removing the Threat
Eradication involves removing malware, backdoors, or unauthorized access from your environment. This may include:
-
Re-imaging systems
-
Patching vulnerabilities
-
Deleting malicious files
-
Resetting credentials
Also document what allowed the breach to happen in the first place to avoid recurrence.
5. Recovery: Restoring Business as Usual
With the threat removed, recovery focuses on:
-
Restoring data from backups
-
Bringing systems back online in a phased manner
-
Monitoring for signs of reinfection
Best practices:
-
Validate systems with integrity checks
-
Communicate with stakeholders (employees, regulators, customers)
-
Track KPIs like mean time to recovery (MTTR)
6. Lessons Learned: Closing the Feedback Loop
Post-incident reviews are crucial. Conduct a retrospective meeting with stakeholders to:
-
Analyze what worked and what didn’t
-
Update the incident response plan accordingly
-
Improve detection and prevention for next time
Use this to build cyber resilience, not just compliance.
Ready to Test Your Cyber Defenses?
🛡️ Don’t wait for an attack to test your response plan.
Schedule a comprehensive cybersecurity audit today to identify vulnerabilities, validate your incident workflows, and align with industry best practices.
Real-World Example: Capital One’s Incident Response Mishap
In 2019, Capital One suffered a data breach affecting over 100 million customers. While their detection systems flagged the anomaly, a delayed incident response process resulted in a larger fallout.
Lesson: Detection alone isn’t enough. A slow or unclear response plan can magnify risks and regulatory fines.
Integrating IR into Enterprise Risk Management
For modern enterprises, an incident response plan shouldn’t exist in isolation. Instead, it should align with:
-
Risk management frameworks like NIST or ISO 27001
-
Business continuity and disaster recovery plans
-
Compliance requirements (e.g., HIPAA, PCI DSS, GDPR)
A coordinated approach improves governance, stakeholder confidence, and regulatory standing.
Is incident response part of risk management?
Yes, it’s a critical component that mitigates the impact of cyber threats and ensures business continuity.
Frequently Asked Questions
Q1: What should be included in an incident response plan?
A: Roles and responsibilities, communication workflows, detection tools, containment steps, recovery procedures, and post-incident review protocols.
Q2: How often should you test your incident response plan?
A: At least bi-annually, or more frequently in highly regulated industries.
Q3: Who is responsible for incident response in a company?
A: Typically a cross-functional Incident Response Team (IRT) led by the CISO or Head of Security.
Q4: How does a response plan help with compliance?
A: It ensures readiness to meet reporting timelines, reduce data loss, and prove due diligence to regulators.
Q5: Can SMBs benefit from an incident response plan?
A: Absolutely. Cyber threats affect businesses of all sizes. A tailored plan improves resilience and recovery.
Cyberattacks are no longer a question of if, but when. The real differentiator for modern enterprises lies in how fast and effectively they can detect, contain, and recover from incidents.
An incident response plan isn’t just a compliance checkbox—it’s a core capability of a secure, resilient business.
Let’s Secure Your Response Capabilities
🛡️ Is your business ready for the next cyber incident?
Book a cybersecurity audit with our experts to evaluate your readiness, assess gaps, and build an enterprise-grade incident response framework.
Schedule Your Audit Now
![]()