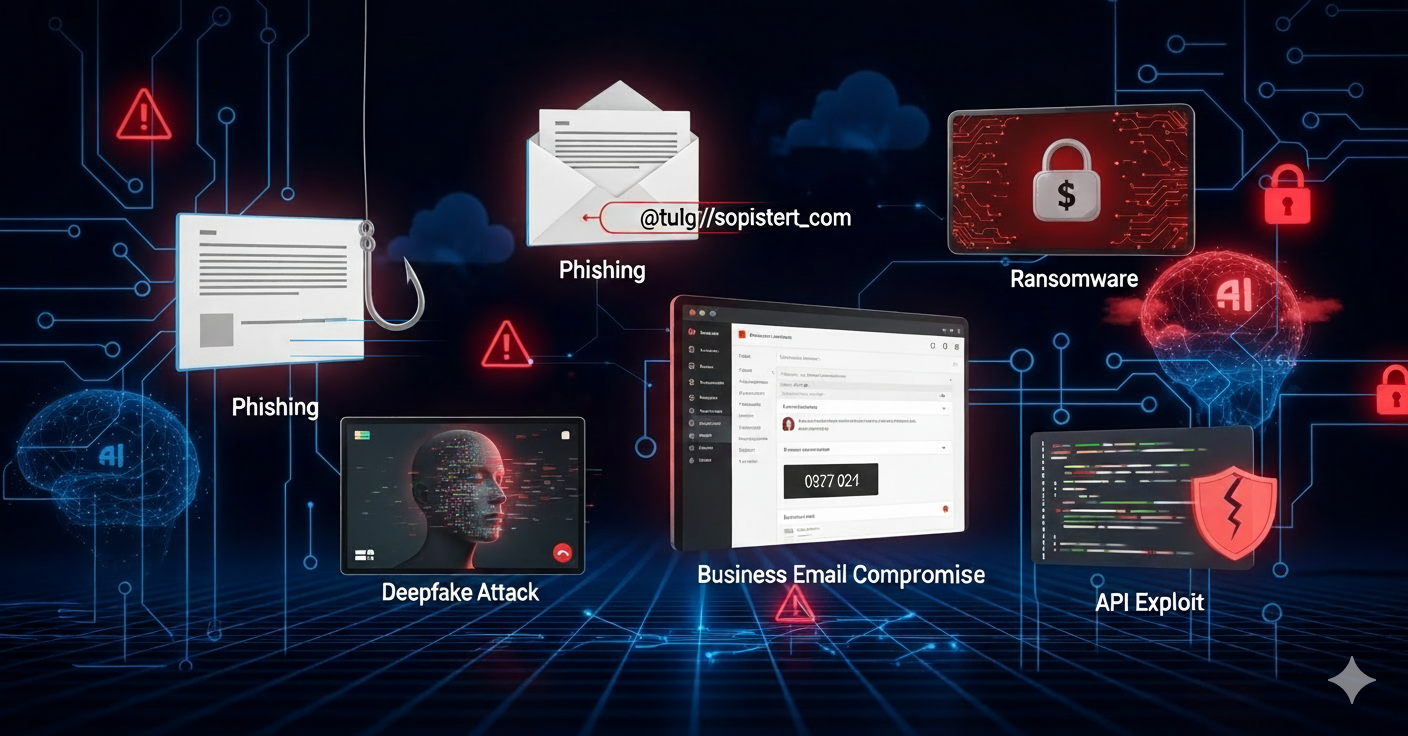
Phishing, ransomware, and business email compromise are still the most prevalent and destructive attacks in 2025.
Attackers are employing AI-created content and deepfakes as a means to circumvent conventional security.
SMBs and enterprises are all susceptible to weak internal controls or unpatched systems.
An informed approach to risk for cybersecurity is imperative to detect, prevent, and respond to the dynamic threats of today.
The State of Cyber Threats in 2025
In the cloud-first, API-first enterprise world of today, cybersecurity is no longer an IT department problem—it’s a boardroom priority. Cybersecurity expenses will exceed $250 billion by the end of 2025, says Gartner, but cyberattacks also continue to grow and evolve quicker than defenses.
With remote work, SaaS sprawl, and third-party dependencies becoming the standard, threat actors have an expanded attack surface to target. This blog discusses the most prevalent types of cyberattacks that companies are experiencing in 2025 and how you can bolster your cybersecurity strategy.
1. Phishing and Spear Phishing Attacks
Phishing remains the #1 attack vector in 2025. But attackers aren’t just blasting generic emails anymore—instead, they’re employing AI-created content and social engineering strategies designed specifically for particular targets.
How do phishing attacks get around email security these days?
Advanced phishing attacks leverage AI to spoof writing styles, create deepfake voicemails, or spoof a trusted domain.
Key Stats:
More than 91% of cyberattacks begin with a phishing email.
Spear phishing attacks strike decision-makers such as CFOs or CISOs with tailored lures.
Mitigation:
Use DMARC, SPF, and DKIM email authentication.
Train staff to recognize AI-generated phishing markers.
Use zero-trust access controls for high-risk behavior.
2. Ransomware-as-a-Service (RaaS)
Ransomware is no longer operated by malicious hackers—it’s a business model. Ransomware “franchises” like LockBit and BlackCat make money by selling tools and technical support to aspiring cybercriminals.
What’s new in 2025?
Ransomware attackers now exfiltrate data prior to encryption, employing double extortion techniques—threatening to publish sensitive IP or customer information unless paid.
Key Targets:
Fintech, healthtech, and e-commerce firms owing to sensitive personal and financial information.
Stat:
In 2025, the average ransom demand is $2.3M, a 37% jump from 2023. (Source: Palo Alto Networks)
Mitigation:
Back up key information regularly offline.
Perform tabletop incident response training.
Apply microsegmentation and behavioral anomaly detection.
3. Business Email Compromise (BEC)
Less showy than ransomware but more financially impactful, BEC is launched by attackers who get into or spoof business email accounts to deceive finance or HR departments into sending wire transfers or updating payment credentials.
Why is BEC more sinister than phishing?
It uses genuine-looking communications that sometimes include genuine hacked-off credentials, which are more difficult to intercept using traditional spam filters.
Real-World Case:
Early 2025 saw a U.S.-based fintech lose $6.8 million following a BEC attack that impersonated a vendor’s billing department. There were no internal approvals followed, and money was wired overseas.
Mitigation:
Implement multi-person approval processes for wire transfers.
Implement AI-driven email anomaly detection systems.
Enforce MFA on all corporate email accounts.
4. API Exploits and Third-Party Breaches
As businesses increasingly use SaaS platforms, third-party integrations and APIs present high-value targets.
Example: A payment API misconfiguration caused enormous PII leakage in a healthtech app, which was attacked using automated botnets that brute-forced credentials.
Stat:
More than 74% of companies had an API-related security incident last year. (Source: Salt Security)
Mitigation:
Take an API-first security stance.
Run ongoing security testing (DAST/SAST).
Validate third-party vendor security controls at procurement time.
Type 5: Deepfake and Social Engineering Attacks
Deepfakes generated by AI are employed during live calls to impersonate partners or CEOs. Increasingly in 2025, voice-cloning cons are employed to trick finance teams or executives.
Example: A COO authorized a secret transfer after receiving what seemed like a video call from the “CEO.” The video was discovered later to be a deepfake based on publicly available videos.
How are deepfakes utilized in business cyberattacks?
Deepfakes are employed to impersonate leaders on calls, particularly for exigent financial approvals or access requests.
Mitigation:
Authenticate requests through secondary channels (e.g., Slack + phone).
Implement real-time call verification tools.
Train executives on deepfake detection.
“Concerned about concealed vulnerabilities?
Avail a free cybersecurity audit today and find out where your business is vulnerable.
Safeguard your systems before attackers discover the loopholes.
A Risk-Informed Cybersecurity Strategy for 2025
Awareness of attack types alone is not sufficient. Enterprises must embrace a risk-informed approach, blending:
Continual monitoring and threat intelligence
Incident response playbooks customized to business risks
Security-by-design practices in product engineering
Board-level reporting on cyber risk as a business risk
Learn more on:
Cybersecurity Strategy Services
Is Your Business Really Secure?
Don’t wait for a breach to discover. Take a free cybersecurity audit today and expose hidden vulnerabilities before attackers do.
Request Your Audit Now
Frequently Asked Questions
Q1: What is the most frequent cyberattack on companies?
A: Phishing is still the most common, particularly spear phishing against high-value targets with highly personalized lures.
Q2: How can small businesses defend themselves from ransomware?
A: Emphasize regular backups, system patching, endpoint detection, and training workers on phishing identification.
Q3: Deepfake scams—do they pose a real threat to enterprise security?
A: Deepfakes are utilized to impersonate executives while on video or voice ccallsfor authenticating fictitious transactions.
Q4: Which industries get most targeted in 2025?
A: Fintech, healthtech, legal, and e-commerce because of the level of sensitive data and exposure to compliance.
Q5: What is the role of APIs in cyberattacks?
A: Insufficiently protected APIs are increasingly becoming a critical attack surface, usually attacked through automation to gain access to information or process transactions.