It’s the illusion of safety that gets you. Because until you’ve seen what Managed SOC Services really do, you might think your security’s already covered.
Think Your SOC Is Enough? Managed SOC Services Prove Otherwise
Security Operations Centers (SOCs) are everywhere now. If you’re a U.S.-based organization, you probably already have:
- A SIEM tool
- Logs flowing into dashboards
- A team reviewing alerts
But here’s the hard truth:
Most SOCs aren’t built to protect — they’re built to observe.
A SOC without response capability is like a smoke alarm that doesn’t connect to the fire department. You’ll know something’s wrong. But no one’s coming to fix it.
Why Most SOCs Fail — and What Managed SOC Services Fix
After working with clients across banking, insurance, retail, and healthcare, we keep seeing repeating pain points. The 5 most common gaps in Mid-Market U.S. SOCs:
- No Real-Time Response
Most SOCs fire alerts, but don’t have playbooks or automation to act on them. - Tool-Heavy, Process-Light
Companies invest in SIEMs (Splunk, Sentinel, QRadar), but not in actual response design. - Compliance Blindspots
Without mapped controls, audits (SOC2, HIPAA, GLBA) become panic moments. - Weekend Vulnerability
Nighttime and weekend breaches go unnoticed — or worse, delayed. - Zero Threat Modeling
You can’t protect what you haven’t defined. Most SOCs lack adversary simulation or attack surface modeling.
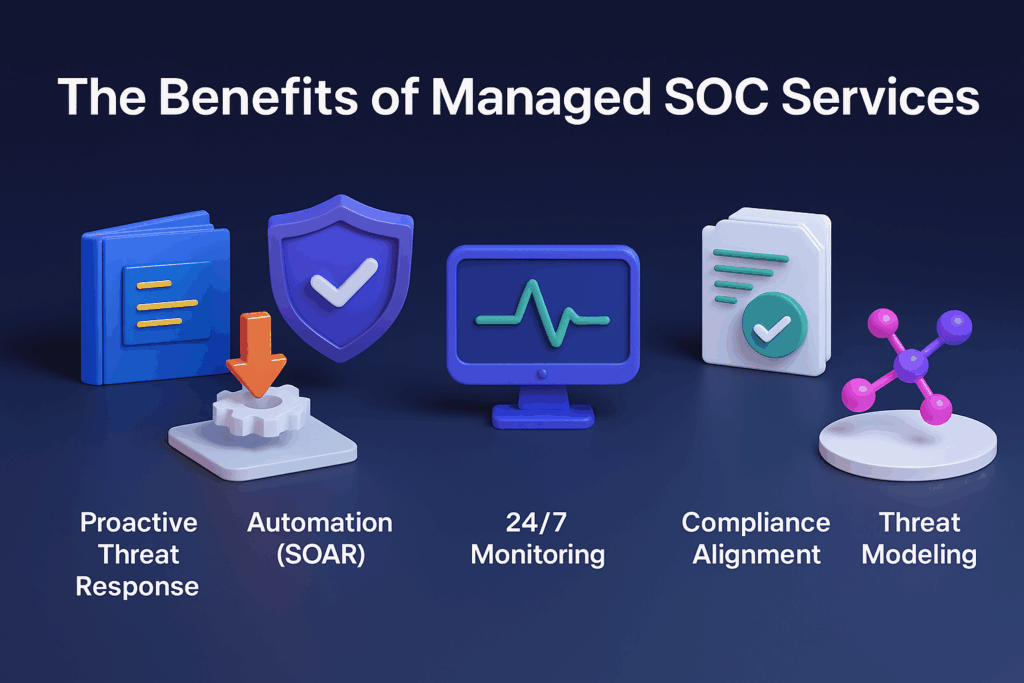
What Managed SOC Services Add That Traditional SOCs Don’t
The answer is:
Proactive Threat Response + Incident Containment + Compliance Mapping
— delivered via a Managed SOC Services that are built to act, not just observe.
In simpler terms, this includes:
- Playbooks: So your team knows how to respond (not just that something happened).
- Automation (SOAR): So response doesn’t rely on human lag or alert fatigue.
- Human Analysts + 24/7 Monitoring: So you don’t sleep through breaches.
- Compliance Alignment (SOC2, HIPAA, etc.): So you’re audit-ready without panic.
- Threat Modeling + VAPT Looping: So your defenses are based on your real risks, not templates.
A Real Example: $10M U.S. Insurer With Alert Fatigue
A mid-sized insurance provider on the U.S. East Coast came to us in 2024. They had:
- Microsoft Sentinel deployed
- A security analyst team triaging alerts manually
- Compliance requirements creeping in (SOC2, GLBA)
But they had no real-time containment, no playbooks, and 200+ alerts daily.
Here’s What INT. Did:
- Tuned their SIEM: Reduced false positives by 62%
- Integrated VAPT: Mapped critical vulnerabilities to live logs
- Built IRP: A complete incident response playbook in 10 days
- Added SOAR: Automated containment on key triggers
- Delivered 24/7: With real analysts & tested runbooks
“We went from alerts to action — and finally felt in control. INT. became an extension of our internal team.”
— CISO, U.S. Client
What’s the Difference Between “Having a SOC” and “Being Secure”?
Let’s break it down:
| Capability | Basic SOC | INT. Managed SOC |
| 24/7 Coverage | ❌ No | ✅ Yes |
| VAPT-Integrated Threats | ❌ Not linked | ✅ Continuous |
| Playbooks for Response | ❌ Missing | ✅ Tested & Tuned |
| Alert Containment | ❌ Manual-only | ✅ SOAR-enabled |
| Compliance Alignment | ❌ Patchy | ✅ SOC2/HIPAA-Ready |
Don’t Start With Tools. Start With Risk.
Here’s the mistake most U.S. IT teams make:
They start with a tool and hope it’s enough.
But real protection comes from mapping risk vectors, not just collecting logs. We always begin with a threat modeling workshop — before recommending any tech upgrade.
SOC Readiness Checklist
If you’re unsure whether your SOC can actually protect you, use this checklist:
- Do we have 24/7 alert triage?
- Do we have a defined Incident Response Plan?
- Are alerts connected to automated actions (SOAR)?
- Are VAPT results mapped to our SOC feeds?
- Do we simulate attacks before they happen?
- Are we confident about upcoming SOC2/HIPAA audits?
Book Your Free SOC Readiness Assessment
We’ll run a quick 30-minute walkthrough to:
- Analyze your alert volume & response gap
- Benchmark your compliance-readiness
- Suggest risk-prioritized fixes (tool-agnostic)
Frequently Asked Questions (FAQs)
A regular SOC just watches. A managed SOC takes action, contains threats, and aligns with business risks — 24/7.
No. Many of our clients use hybrid or fully managed models with fractional experts from INT.
Absolutely. A Managed SOC maps threat workflows directly to SOC2, HIPAA, GLBA, and other frameworks.
We offer flexible monthly models for startups to enterprises — and start with a free readiness audit.